Ncp For Mac
NCP: Normalized Coefficient of Probability: NCP: Natural Cane Products: NCP: National Collections Program (Smithsonian Institution) NCP: Net Control Procedure: NCP: Naval Capability Pillars (US Navy planning concepts: Sea Strike, Sea Shield, Sea Base, FORCENet) NCP: Naval Communication Plan: NCP: Network and Communications Provider: NCP: N. Best price Mac Os Sonicwall Vpn Client And Ncp Vpn Client For Android You can order Mac Os Sonicwall Vpn Client And Ncp Vpn Client For Android after check, comp. The NCP Secure Enterprise macOS Client 4.0, the NCP Secure Entry macOS Client 4.0, and the NCP Exclusive Remote Access macOS Client 4.0 include a network adapter for IPv4/IPv6 and provide full compatibility with macOS Catalina 10.15. The new macOS Clients are also certified by Apple. NCP has also extended IPv6 support in its VPN client. NCP Solutions helps companies optimize the effectiveness, efficiency and impact of their business-critical communications. For more than 45 years, companies have relied upon our industry-leading expertise, freeing them to focus time, energy and resources on their core business needs and on what matters most to them – creating value for their customers. Shop for How To Setup Cisco Ipsec Vpn On Mac 10 13 And Ncp Secure Entry Client Cisco Vpn How To Setup Cisco Ipsec Vpn On Mac 10 13 And Ncp Secure Entry Client C.
 Resolution
ResolutionOverview

Ncp Machine
The NCP Secure Entry Client is an IPsec-compliant third-party application that can be used to establish a connection to a GlobalProtect Gateway using either a PSK or certificates with XAUTH. Versions are currently available for Windows, Mac OS X, and Android operating systems. The instructions below pertain to the Windows client and assume that the GlobalProtect Gateway has already been configured on the Palo Alto Networks firewall. Otherwise, refer to How to Configure GlobalProtect.
Steps
- Open the NCP Secure Entry Client and go to Configuration > Profiles.
- Click the Add / Import button.
- Choose the Connection Type.
Select Link to Corporate Network Using IPsec.
- Choose the Profile Name. Enter an alphanumeric name for the connection profile.
- Choose the Communication Medium. Select the proper Communication Media depending on how the client connects to the internet. The two most common options are LAN (over IP) for Ethernet and Wi-Fi for wireless connections. The NCP client will automatically select the connection media if automatic media detection is selected.
- Set the VPN Gateway Parameters.
Gateway (Tunnel Endpoint): the DNS name or IP address of the GlobalProtect Gateway configured on the Palo Alto Networks firewall.
Check the Extended Authentication (XAUTH) box. Enter a User ID and Password that can be authenticated by the Palo Alto Networks firewall.
Ncp For Macrosomia
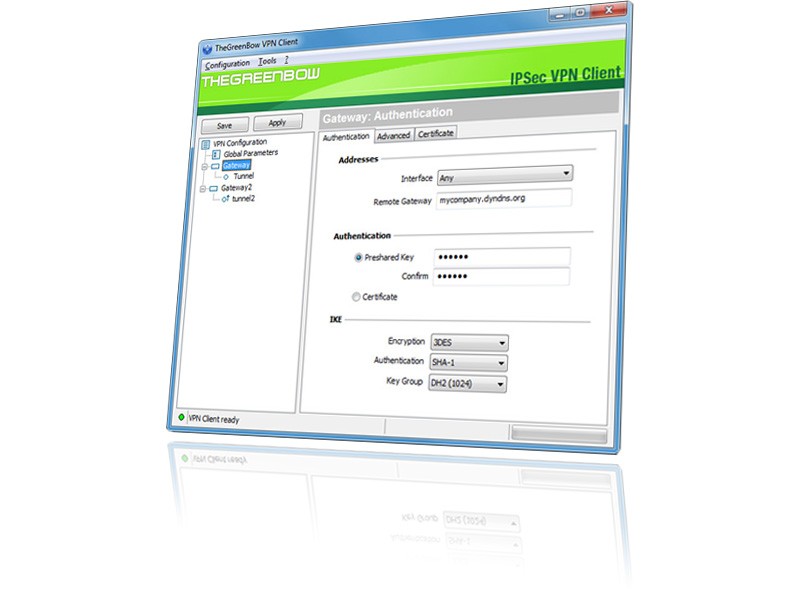
- IPsec Configuration.
Exchange Mode. For PSK authentication, select aggressive mode (IKEv1).
For certificate authentication, select main mode (IKEv1).
PFS Group: none
Pre-shared Key
Local Identity (IKE):
For PSK authentication:
Type: select Free string used to identify groups.
ID: enter the Group Name configured under Network > GlobalProtect Gateways > Client Configuration on the Palo Alto Networks firewall.
For certificate authentication:
Type: select ASN1 Distinguished Name.
ID: leave this field blank.
Pre-shared Key (required for PSK authentication only):
Shared Secret: enter the Group Password configured under Network > GlobalProtect Gateways > Client Configuration on the Palo Alto Networks firewall. The configuration for PSK authentication is shown below.
- Configure the IP Addresses
IP Address Assignment: select IKE Config Mode.
Don't modify the DNS Server or WINS Server fields.
- Set up the Firewall. Select the desired Stateful Inspection setting and click the Finish button.
If using PSK authentication, the configuration is complete and you should be able to connect to GlobalProtect Gateway.
Ncp Manchester
- Export the root and client certificate from Device > Certificate Management > Certificates on the Palo Alto Networks firewall.
Note: This step is not necessary if an external CA is used, but the root certificate must be DER encoded and the client certificate must be in the PKCS#12 format.
Export the root certificate in the Binary Encoded Certificate (DER) format.
In the NCP client, go to Configuration > Certificates.
Click the Add button.
User Certificate
Name: enter a name for the certificate configuration.
Certificate: select from PKCS#12 file.
PCKS#12 Filename: browse to the client certificate exported from the Palo Alto Networks firewall.
(optional) Check the PIN Request at each Connection box if you want the user to enter the client certificate Passphrase before every connection attempt.
Click the OK button.

- In the left menu, select Identities.
- Certificate Configuration: select the certificate configuration you created earlier.
- Click the OK button.
17. Move the exported root certificate into the NCP > SecureClient > CaCerts directory. The default installation path is C:Program Files (x86)NCPSecureClientCaCerts.
You should now be able to use the NCP client to connect to the GlobalProtect Gateway using certificates and XAUTH.
Attachments
